As we all know the new pandemic has brought with it a new explosion in the use of networks. Due to this problem, all companies have been forced to implement teleworking and new forms of communication between their teams and personnel. This, together with the wave of confinement and the problems of exposure to contagion, has multiplied the use of computerized software such as online stores, social networks, video streaming services, etc…
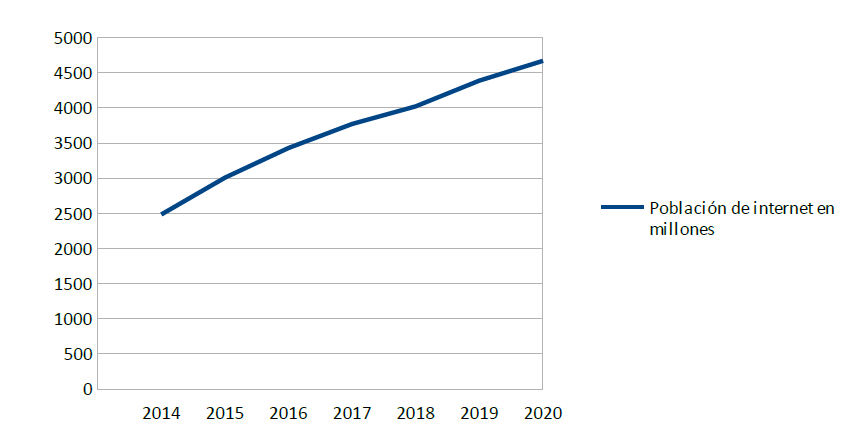
As we can see in this graph, the Internet population has grown exponentially since the beginning of the pandemic, but also with the pandemic the digital population has increased even more.
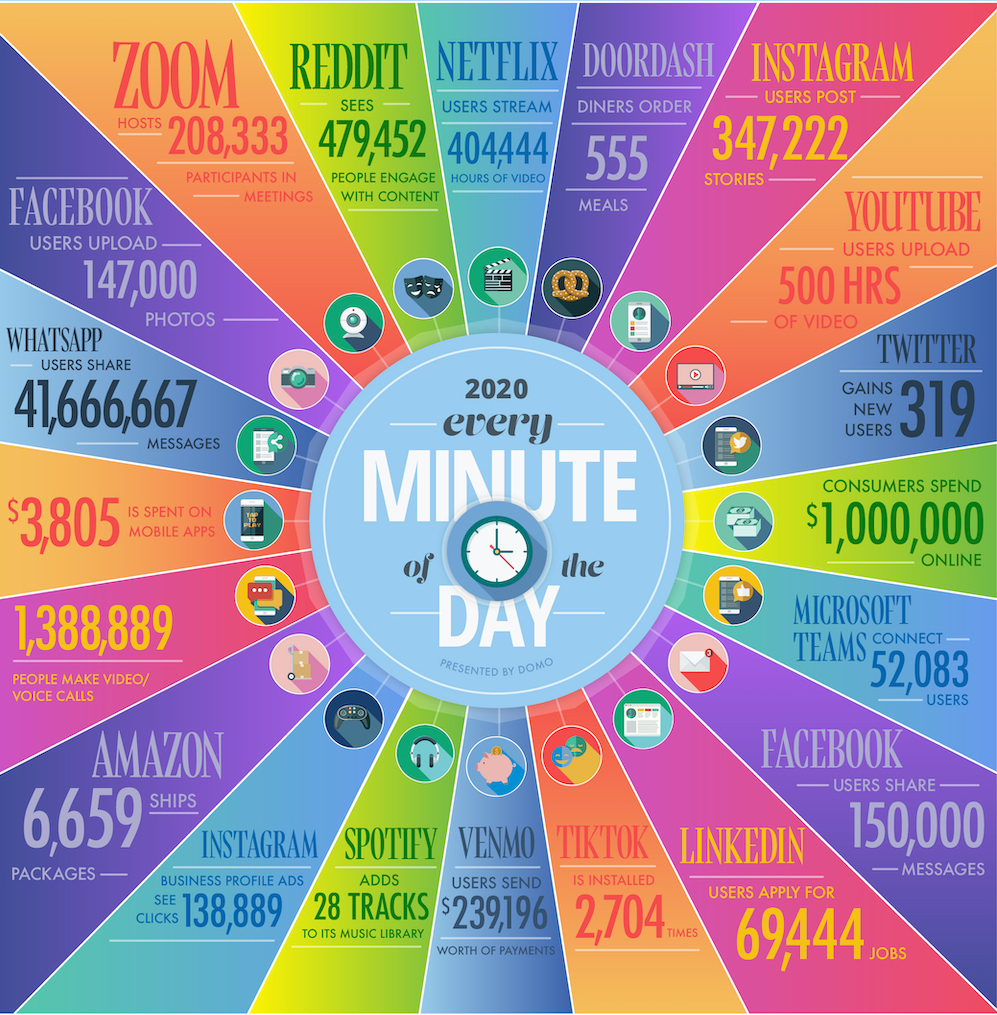
Specifically, to give you an idea of the activity that happens on the Internet, I show you this infographic from the Big Data and AI company domo, in which we can see what happens on the Internet every minute. With this you can get an idea of the information that moves through this network every day of your life, while you watch Netflix, use Facebook or just read the mail.
The fact that this network is growing at such a high rate and has so much data exchange activity makes it susceptible to certain risks. Just as in normal life, we are faced with people who try to take advantage of us or deceive us in order to take advantage of the situation. Internet is not exempt from this type of practices, but it is multiplied by the fact that the person who carries out this action feels safe and hidden, behind the virtual layer that this offers. That is why from the IT department of Gabitel we want to bring you this news that we hope will help you and clarify any doubts you may have about the digital world.
When we expose ourselves to the digital world today, we are exposing all our business, economic and social information out in the open. This means that we must be especially careful with our accounts and our data, because in an oversight we can put at risk our data or our economy. Allowing that malicious people can do us a serious damage. For that reason we recommend you to dedicate special attention to this guide and to the practices that we propose you in her.
Always distrust the sender
Throughout the day, both at work and in our modern life, the use of email has become something more mandatory than necessary, it is a simple and low cost communication that is available to everyone, so it is rare the person who today does not have this type of system, but … What danger can we find here?
Many of you will have seen hundreds of advertising e-mails in your inboxes, this in principle does not generate more than a slight annoyance, but some time ago a new variable came into play, the spoofing. As with SPAM, this practice is based on sending mass mailings, only this time they do not want to sell us something, but to pass for someone we know, so that through “social engineering” we end up opening a link in the mail or an attachment. This ends up putting our information at risk, since the first target will be our emails and the information in them. That is why we are going to recommend you some practices to avoid falling into this deception and to act in case of having fallen.
What to do if we have not yet opened the mail
Most important of all, whoever the courier is from, always be on the alert. Therefore, always be suspicious of the messenger. Check that the email address from which it comes is known to you or corresponds to the content of the email. For example, it will not be normal to receive mail that asks about an invoice with an address that you do not know at all. To find out this information you only have to look at the “FROM:” field of your email client, usually near the name, which will be the one they use to try to trick you.
On the other hand, and not less important, always have a cool head, this type of attacks usually take advantage of our fear or our laziness. Therefore always think logically when you read an email, if you notice something strange or does not fit, avoid opening links and attachments.
We have opened the link
The best thing is to warn our acquaintances that they will receive mail pretending to be us, examine the PC in search of virus and change the password of the mail as soon as possible. As before, you must keep a cool head, know that you have made a mistake, but act quickly and decisively. When changing the password it is also important to follow some rules, not only with the e-mail but with all the online accounts that we have, we will not be the first or the last ones that have been hacked and have lost passwords in the event.
Let’s talk about the keys
As the Internet grows, as is normal, we will be overwhelmed by the number of customer accounts in different services. For example, social networks, stores, email services, etc.
Therefore it is good to be tidy, keep everything updated and safe. The first thing we recommend is to use a password manager. This type of software allows you to have only one master password in your head while it acts as a “vault” for all your user passwords. A good example of this would be Last Pass, is a service that we use a lot in the department and it works very well. It is important to keep in mind that the master key must be secure or we will be selling our soul to the devil.
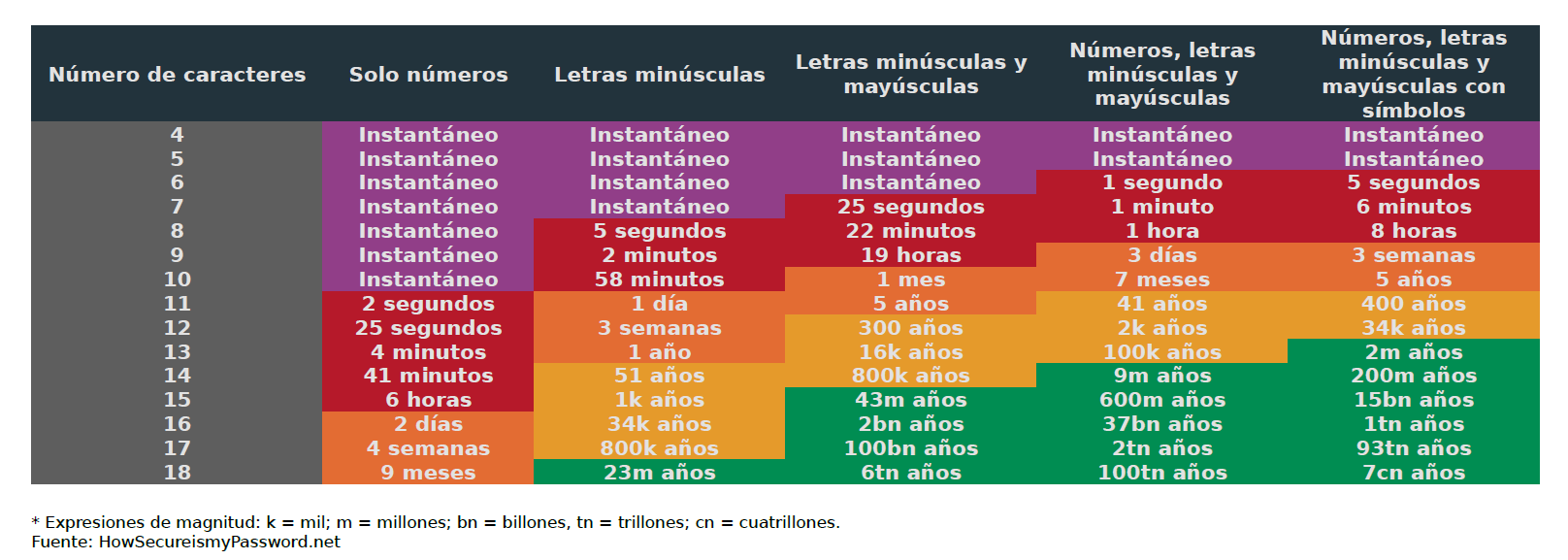
When creating a key it is important to take into account some concepts, for example, the length of the key and the type of characters used. Here I show you a table that we have created with the data from security.org, where we can see how long it would take to try all the combinations of our passwords with a brute force program. The ideal is to have passwords that are in the green zone, to avoid that thanks to the latest technological advances our passwords can be discovered too quickly for us to stop the attack.
In addition to this you should always keep in mind some tips like these:
- Avoid using the same password for several different users.
- Do not share your passwords with strangers or send them by email.
- Change your passwords at least every 6 months.
- Never use pet names, dates of birth or data easily known by others as passwords.
By following these simple guidelines we should not have any problems with our accounts, but as always there can be more dangers than just having our password cracked. As we have seen in the chapter on e-mail, we can be exposed to malicious software, more commonly known as virus, although within this there are a multitude of varieties.
Defense against computer viruses
Avoiding this type of infections can become a real challenge, since many of the most common practices can lead us to be exposed to this type of risk. Let’s talk a little about the types of users that we can find when we talk about bad practices as far as viruses are concerned.
The negationist
There are users who believe that it is not necessary to have an antivirus, or think that it is not relevant software on a computer. Unfortunately for these users they could not be more wrong, since, many of the efforts of the pirates are concentrated in developing software that cannot be detected and to take all type of advantage of this, obtaining information of the user of an illicit form. That is why it will always be necessary to use this type of software, even if it is free, in order to be protected against possible new infections.
The minesweeper
Most users in their life have used unlicensed or “pirated” software, it is a common practice to save money, test a product or simply out of laziness. When a user carries out this practice, he is literally playing Minesweeper, since many pirates take advantage of the need to download illegal patches for these programs and put malicious code in them. In addition, when surfing this type of website, the computer is exposed to the execution of malicious code from the website itself, since it is not the first case of websites that collect user data illegally or use your PC for their own purposes. That is why we will also look at the latter type of user.
The diver
Surfing the web can be one of the most fun things we have at our fingertips today, in it we can find stores, entertainment, multimedia and knowledge of all kinds, but this does not make all websites are safe. As it happens in the world, where there are sites more dangerous than others, surfing the web we can find dangerous pages, a way to avoid putting ourselves at risk, is to always look at the padlock that we see to the left of the address of the page. If this padlock is closed, it means that the web is protected by encryption, which means that the data that we introduce in this one are hidden to the observer.
Another of the dangers that we can find on the web are the trackers or tracking cookies, when we navigate it is important to be aware of what we admit of this, since many websites will try to put in our browser small pieces of information to have us located and know more about us. This can be avoided by denying the cookies in webs that are not of our confidence.
Last but not least, there is the new abuse of notifications. More and more websites are asking you to accept notifications, this is a new practice that, although it does not include a high risk, can become very annoying because on many occasions we can be bombarded or receive SPAM of this type.
To finish we leave you with a curiosity on computer science: the term SPAM that identifies to the junk mail, comes from a product of canned meat that consumed the army of the USA in the second world war, was so common the publicity of this product and its quantity in the supermarkets and homes of the USA that the group of British comedians Monty Python made a sketch on the product in its series Flying Circus and thanks to this its use was popularized in the world of the computer science decades later of the launching of the product.
We hope that the information is useful and that it helps you in your day to day in the digital world, greetings to all of you.